Once malware or a malicious exploit has bypassed your defences and run on your system, it may establish a foothold that ensures it will continue to run, even after reboots or the user logs off. This type of threat is known as a persistent foothold. EDR/MDR software can identify and neutralise these types of persistent threats.
How does a persistent foothold work?

For a persistent foothold to be established, a user would typically be the victim of an e-mail exploit, drive-by download or a similar exploit which results in malicious software running on their device. A foothold is typically established as soon as preventative defences (i.e. antivirus) are evaded and initial access has been established (i.e. the malware has launched).
Once the attacker has access, the malware will use a persistence mechanism to ensure it can repeatedly run, even after a reboot or the user has logged off. These persistence mechanisms allow them to ‘return’ and regain access at a later date, or they may act as an access broker, selling access to your system on a hacking marketplace.
What are some examples of persistent footholds?
Persistent footholds can typically be grouped into the category of ‘autoruns’. In Windows environments, there are many mechanisms from which malicious software can run:
- Scheduled tasks.
- Registry keys
- Startup items.
- System drivers.
Should my antivirus stop persistent footholds?
Yes and no. Often the initial attack vector (a malicious e-mail, drive-by download, or similar exploit) may not trigger your antivirus software. After the initial attack, the persistence mechanism may not be malicious enough to be identified. Microsoft Office macros, malicious scripts and zero-day exploits are often the sources of malicious payloads.
Can you detect persistent footholds?
Modern MDR (managed detection and response) software will identify and remediate persistent footholds while alerting you (or your IT provider).
How common are persistent footholds?
We regularly see persistent footholds in the wild, particularly when we begin working with new clients.
MDR software is part of our managed IT software stack; when we deploy MDR software into a new environment, one of the first things we look out for is footholds. In many cases, these footholds date back years (and are dormant), while they are still active in other cases.
What are the dangers of persistence?
The longer an attacker has access to a device, the more intel they can gather and the more damage they can do later.
11 days is the average dwell time before an attacker is typically discovered. [Source Sophos]
How can I check (and defend against) persistent footholds on my systems?
We offer two solutions that check, monitor and safeguard against persistent footholds. With both of our services, you benefit from having 24/7/365 threat response and remediation services from industry-leading SOC teams (security operations teams).
- We provide an advanced EDR (Endpoint Detection and Response) solution that uses AI, data science, and our partner’s global SOC team to identify and respond to any incidents or indications of compromise (IOC).
- We also work with a partner who has a sophisticated MDR service specifically focused on persistent footholds. They operate a 24/7/365 SOC with near-instantaneous response and remediation services.
Both of our MDR services are licensed per device on a monthly subscription.
Where does MDR software fit into my existing security architecture?
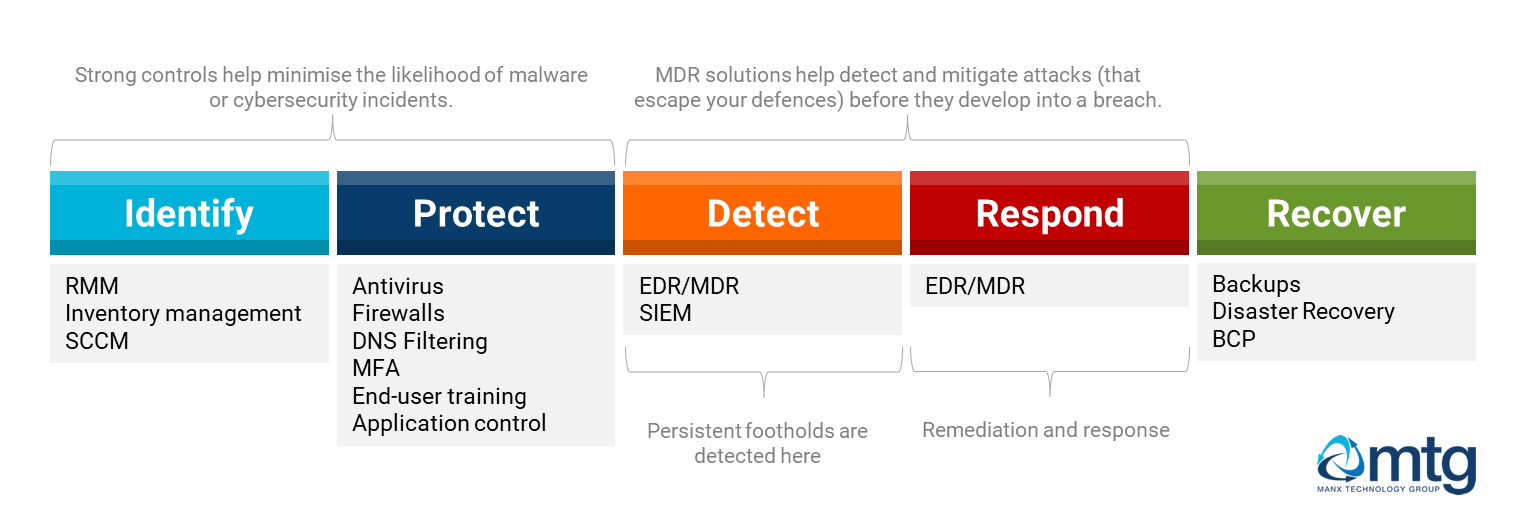
The NIST Cybersecurity framework defines five core functions, also known as the Framework core.
- Identify
- Protect
- Detect
- Respond
- Recover
EDR/MDR solutions provide stronger coverage in the detection and response areas – helping to identify threats proactively and helping you avoid a worst-case scenario.
What else do I need to consider?
As with everything when it comes to cybersecurity, you need to focus on all aspects of information security:
- Patching and systems updates.
- End-user training.
- Configuration hardening.
- Authentication and 2FA.
- etc.
It is also worth noting that more and more cyber insurance policies recommend, or mandate, the user of EDR/MDR software.
Find out more (and find out what could be lurking!)
Please get in touch with our sales team to ensure your business has a clean bill of health and is protected against persistent footholds. We can install our MDR platform on your systems, undertake an assessment and (if required) remediate any footholds.