
When you read a small business firewall datasheet or brochure, you may be confused by the terminology or lost in the wealth of performance metrics quoted. This problem is often made worse when different vendors use subtly different terms or use a different basis to assess performance!
We hope this blog post is useful and gives you an insight into the different features of a small business firewall.
If you or your business needs assistance with a firewall project or considering an investment in a managed firewall for an SMB/SME, get in touch.
We can provide complete firewall solutions or consultancy to assist with your project. For larger projects (i.e. multi-site, VPN, high-availability) we can work on a project basis.
What figures matter when selecting a firewall? Which feature sets should you be most concerned about, and those that, frankly – shouldn’t matter so much! This article will define those items, explain their significance and outline how to map this against a challenge or risk within your business.
If your business has a need to enhance its firewall or network security, or you need assistance in selecting the right firewall solution – speak to MTG and our team of firewall engineers.
Firewall Throughput
This is typically quoted as Mbps (megabits per second) or Gbps (gigabits per second). This is the volume of traffic that can pass through the firewall at any one time. This is an important metric, but in many respects – worthless. This is evidenced by the fact that most figures cited in manufacturer data sheets will have caveats or asterisks (*) after each figure. Why? This is raw throughput, the measurement of traffic flowing through the firewall without necessarily being subjected to antivirus scans, content filtering, intrusion prevention, data loss checks and similar steps. The figure can also vary by protocol and packet size. Some vendors may cite 1500 Byte TCP whilst others 64 Byte UDP!
Throughput is even more important for internal network segmentation. When a firewall is deployed as an internal network segmentation firewall, it controls traffic flowing between internal networks and/or VLANs. You can read more about INFWs here.
Nowadays, most firewalls (even SME models) will support traffic levels of 1Gbps+ however, most internet connections will be far less than that. Make throughput a consideration, but focus more on the other throughput figures outlined later.
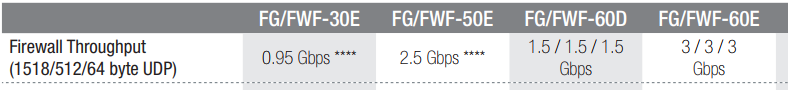
Also known as stateful inspection throughput, firewall bandwidth, etc.
IPSec Throughput
If your business uses site-to-site VPNs, IPSec throughput is the amount of network traffic that can pass through the firewall and the encrypted tunnel to your remote site (or users). Nowadays, most decent firewalls use hardware encryption so IPSec figures should be similar to the overall throughput of your device. If your business has many sites and IPSec VPNs are a logical part of the business, then this is an important figure to consider.
To stress, your firewall cannot route traffic faster than your internet connection! If your internet is 100Mbps and your firewall can handle 5Gbps of IPSec, you have a bottleneck! Naturally, always build in headroom (i.e. 50Mbps VDSL -> 200Mbps IPSec).
Also known as Triple Data Encryption Standard (3DES), AES, VPN Throughput
VPN to Azure or AWS
Most leading firewalls support the connection of offices and on-premise environments to Microsoft Azure or AWS using VPN technologies. We regularly build IPSec VPN tunnels from firewalls installed in offices, to VNETs hosted in Microsoft Azure. This hybrid approach provides a method in which organisations can gradually migrate to the cloud, with seamless connectivity between the two.
Working from home support
When your business has a requirement for staff to work from home, but still have access to internal IT systems – VPN access is the ideal technology. SSL VPN access allows staff to use their own laptops or desktop PCs to access the workplace. You can read more about VPN technologies below.
SSL VPN Throughput
Similar to IPSec, this is the throughput the firewall supports for users who have connected in to the business using SSL VPN/remote-access. The same rules apply. Your internet connection is the first bottleneck, so 50Mbps internet and 1Gbps SSL throughput needn’t be important. The other important consideration is the amount of bandwidth and applications that your staff will be using when they do access systems remotely.
If you use a bunch of Citrix/RDS, then traffic levels will be in the Mbps rather than Gbps. However, if they pull down significant amounts of data, these figures will be far higher. Unlike IPSec, many firewalls have far lower SSL throughput levels so this is an important metric to consider. Generally speaking, calculate the number of concurrent remote access sessions and try and understand their bandwidth usage.
Also known as remote-access throughput, ANYConnect performance
Remote Access Users / SSL VPN Connections / Max Supported Users
This is simple, how many concurrent users can “connect” to your firewall (from outside the organisation) at any one time. When selecting a firewall, consider how many of your staff will work remotely and need to connect in from home or when on the road. Also, consider a DR scenario where you cannot access the office premises. As with everything, build in some headroom for growth and consider alongside the throughput figures.
Also known as remote-access users, SSL VPN users, AnyConnect users.
SSL Inspection Throughput
When your firewall scans web traffic, often it is unable to scan encrypted SSL sessions (i.e. to banks, Gmail, etc). Many viruses and threats pass through encrypted channels so a number of firewalls such as Fortigate will actively scan encrypted traffic for malware. To do so, the firewall needs to decrypt, scan and then re-encrypt traffic on the fly. SSL Inspection throughput is the figure that describes how much traffic it can scan at any time. Entry level Fortinets, this can be 35Mbps! whilst higher end models 300Mbps – this is important if you want to ensure scanning at every level, across all protocols.
Zero Trust Network Access (ZTNA)
ZTNA is a relatively new concept now supported by firewall vendors, and it is expected more and more customers will shift from VPN to ZTNA network access.
AV (Antivirus) and IPS Throughput (Intrusion Prevention System)
For firewalls with an antivirus (AV) or intrusion prevention system (IPS) engine, these systems actively scan traffic for viruses, malware or patterns that may indicate a hacking attempt. As before, there are hard limits to how much traffic can pass through these features.
These are important if the purpose of your firewall is to safeguard your business. If your firewall supports 1Gbps of raw throughput but only 50Mbps of AV/IPS throughput, that is your lowest common denominator! For most SME/Enterprise, we recommend scanning and profiling web and e-mail traffic, which makes up the majority of an organisation’s usage profile.
When considering a firewall, pay particular attention to these figures as they will deliver real benefits to the business. When calculating, consider your connection speed and the typical usage profile of your users. This can be measured in existing environments. Some figures may quote one protocol (i.e. HTTP) and omit HTTPS – which is subject to SSL inspection throughput.
Examples of IPS traffic would be:
- IPS and SSL inspection on your inbound rules for Microsoft Exchange and OWA. Signatures from Fortinet (or your firewall vendor) could defend against zero-day attacks (i.e. Hafnium) or brute-force attempts.
- IPS can also protect clients on your LAN, it could be malicious actors hosting PDF documents that attempt to exploit Acrobat reader.
- SSL inspection is used for inspecting the content of web traffic, identifying threats, but also applications.
Other Throughputs (NGFW, Threat Protection)
Always consider throughput against your internet connection, typical usage and user profile.
Firewall Latency

When traffic flows through the firewall, the latency (typically cited as a millisecond or microsecond µs) is the time it takes for the packet to pass through the device and be screened against its security policy.
High-performance firewalls are typically in the low microseconds (µs), for example, the FortiGate 81F can process traffic at 3.23µs. Does this really matter for a small business? Not really. There are always exceptions, but any firewall that can process traffic at less than a few milliseconds is fine for the average SME.
Concurrent Sessions
This is the total number of concurrent connections that can be open at any time. Each time you browse a website such as CNN, Google Chrome may open 20 x different connections, to download images, videos and stylesheets from different sources.
As I write this article, my laptop has around 80 x connections open (through a mix of websites, apps, e-mail, etc).
An entry-level FortiGate 40F supports 700k concurrent sessions whilst an FG-81F supports 1.5m concurrent TCP sessions., Even in an organisation of 800 staff, with servers, infrastructure and power-users, that leaves sufficient headroom. If you are wishing to upgrade your firewall, the number of concurrent sessions can be reviewed on your existing firewall (get in touch if you need assistance with this).
New Sessions/Per Second
This is how quickly your firewall can allow an additional connection through the device, and subject that connection to the security policy. Typically these figures will be “x” thousand sessions setup per second. An entry-level firewall will be able to do a few thousand (i.e. 4000) whilst high-end firewalls 100k new sessions/second.
The typical usage profile for an SME or enterprise is such that you would typically not expect an aggressive onset of new sessions (beyond 4000) however, a higher figure is indicative of the firewall’s performance – but it is unlikely to be the primary focal point when deciding. Like concurrency, new sessions/second can be measured.
Management
How do you manage the firewall? Web access, management application, cloud service or over the CLI/SSH? Also, ask whether you want to manage/configure the firewall or use a specialist business to configure and manage the firewall for you.
Web access is most common, however, a good CLI should be considered for complex (or even convenient) configuration.
Many modern firewalls some ‘cloud management’ which allows you to manage multiple firewalls from a single location. Cloud-managed firewalls are a great solution for when your firewalls are deployed across multiple offices or sites.
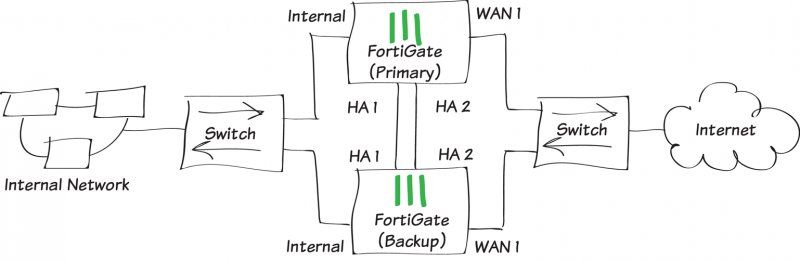
High Availability / Clustering
With a single firewall, it is the sole gateway for your business to the internet. If it fails, you cannot access the internet (easy to understand!). With high availability, your business would purchase two firewalls that operate in harmony in an active/active or active/passive state. In effect, if one fails, the other takes over. This is typically a seamless process.
When considering a Cluster or HA pair, you must consider what is upstream of the firewalls (i.e. your ISP router) and downstream (your network switches). Having redundant firewalls connected to a non-redundant switch just shifts the risk element and point of failure. When considering HA, you must consider the wider operating environment and risk factors. An example of HA is available on the Fortinet Cookbook website here.
Firewall Policies
This is the number of rules you can have configured on the device. Rarely is this an issue for any business we have worked with. Fortinet supports a minimum of 5,000! For the SMB, less than 20 rules are typical. For the SME, perhaps 25-150 maximum. Whilst an enterprise or hosted environment may have several hundred. You can quickly see why 5,000 rules gives you some headroom!
Hardware vs Virtual
For businesses running VMWare or Hyper-V, you needn’t buy a physical device. Instead, you can have a special software appliance that acts as your firewall. This doesn’t reduce your security, but it does mean you need to route your network traffic through a virtual environment.
This may sound a little hard to wrap your head around, however, for small businesses – a hardware firewall probably makes more sense. Virtual firewalls are great, but require a level of expertise, an IT department or firewall partner to make them work for you.
Interfaces
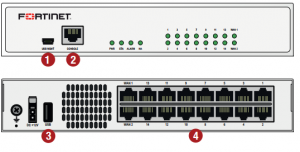
How many network ports the firewall has, and what speed. You shouldn’t consider anything other than Gigabit (GB). Wireless is a nice feature, but not strictly required by every business who may choose not to want wireless or has an existing solution. Although wireless support may appear slightly more expensive, consider it will be secured and subject to the same network policies as your other traffic. Often integrated wireless for SMB/SME is a great addition on a proper firewall.
If your firewall is being deployed as an internal network firewall, then you should really consider 10GE interfaces as a minimum.
Power-supplies
Where uptime or redundancy is important, consider two power supplies. Many firewalls may have a single PSU (in which case, keep a spare), a single PSU but with a secondary external port (so you can use an external PSU as a backup) or higher-end firewalls have two native PSUs for ultimately redundancy. Many firewalls use external DC supplies which are relatively inexpensive and so it makes sense to have a spare.
Application Visibility
Traditionally firewall policies are based upon rules that relate to TCP and UDP ports, rather than the application and user activity within those traffic flows. Modern firewalls allow you to create and enforce firewall policies based on the actual application in use. For example, you can allow access to Microsoft 365, block Skype, WhatsApp and other undesirable applications. Doing so takes the hassle out of firewall policies, looking up IP blocks and so on.
Web Filtering
The ability to monitor website and control web browsing activity is a popular requirement in business. Web filtering controls allow you to monitor productivity or to prohibit access to high-risk or illegal web content. Website filtering is supported on the majority of firewalls with next-gen or UTP (unified threat protection) capabilities.
SD-Wan
Software-Defined WAN is a virtual architecture that allows your business to use a range of connections (i.e. fibre, DSL, 4G) to connect to the internet and your other sites. In simple terms, the firewall has functionality that allows you to manage traffic flows over these links subject to a range of criteria. Examples could be quality of service, connections to cloud applications such as Office 365 and AWS, or automated failover in the event of an outage. Many larger businesses are choosing to replace expensive carrier-grade WAN and MPLS services with SD-WAN solutions.
MFA (Multi-factor authentication)
A no-brainer for network access. Check the firewall you are selecting supports MFA or 2FA technologies. The MFA may be vendor-specific (i.e. FortiToken) or it may support a solution such as DUO. We recommend all VPN access is secured using MFA.
Geo-Location support
Being able to restrict network access or traffic to specific countries is a great way of enhancing security, with low-overhead. If your services should only be available to the UK, limit the traffic to the UK. While security through obscurity is not bullet-proof, it is an added control that can be used alongside other forms of best-practice.
Local Storage
Low-end firewalls have no local storage, this means logs, charts and reports are not supported, slow or rely on an external web service or software suite. Firewalls with local storage typically have better reporting, responsiveness and log capabilities. This is a generalisation however if you plan to work on your firewall regularly and inspect logs/reports, a firewall with local storage is a must (or a robust cloud service). When purchasing a firewall, look to see if it includes onboard disks or SSD drives.
Form Factor

A simple one. Is it desktop mount (i.e. on a shelf) or rack-mounted, goes in a rack. You can often buy third-party rack kits for desktop form factors (or a shelf!)
4G/Mobile
Many firewalls have a USB port that can accept a 4G mobile dongle. This provides an additional WAN port for internet access in the event your DSL or fibre fails. Pay important notice of the supported dongles, modes of operation and limitations.
Third-Party Certifications
Many vendors put their firewalls through independent testing to prove their throughput, capabilities and protection systems. These include bodies such as ICSA and NSS Labs. The tests can be against AV, firewall, IPSec, SSL and IPS. Whilst not the single important factor, independent validation can provide additional proof and endorsement.
Technical Support and Hardware Warranty
Once you have invested in your firewall, it is important to understand what assistance is available if things go wrong. For example, in the event of a hardware failure – what can you do? Or, you hit upon a bug that results in some strange behaviour – how do you obtain software updates?
There are generally three types of support/subscription:
- Standard hardware warranty. RTB (return to base) warranty means in the event of a hardware failure, you will send the hardware firewall back to the manufacturer for a replacement. The exact terms of the hardware warranty may vary by your country.
- Enhanced hardware warranty. Enhanced warranty gives you access to express hardware support. In the event of a hardware failure, the vendor will proactively dispatch a replacement that you can implement, before returning the failed firewall. You also gain access to the vendor’s technical support team for queries relating to configuration, bugs and updates.
- Enhanced hardware warranty and UTM subscription. An ongoing subscription gives you all over the above, but provides real-time updates to your firewall for things like virus definitions, protocol signatures, application signatures and threat intelligence. Often the annual cost of a security subscription can be up to 30% of the initial cost of a firewall. These costs need taken into account when sizing your firewall and calculating your budget.
(Note: If your business cannot tolerate downtime due to a failed device, you should consider a firewall cluster – where the devices operate in a redundant pair)
End of Life / Retirement
How new is the firewall? When will the firewall reach EOL (End of Life) or be retired? There is always the balance between buying a mid-life, proven and hardened firewall VS a beading edge, potentially buggy firewall. This really varies by vendor and how robust their QA processes in. I would tend not to buy an old firewall as business requirements will overtake its capabilities very quickly. Regardless, this should be a consideration when selecting a firewall.
Benchmarking and Group tests
Research third-party reviews and evaluate group tests between vendors. We regularly compare Fortinet vs Sophos vs Cisco vs PaloAlto. Our engineers, although adept with Fortigate, use all of the aforementioned vendors as part of their daily jobs. Tests and reviews need to be taken with a pinch of salt, often there is a particular feature or service that will really benefit your business, but not someone else’s. Good sources include NSS Labs, SC Magazine, PC Pro and ICSA.
Read the small print
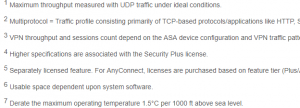
Nearly all key performance criteria will be subject to a caveat. It may depend on your applications, “ideal conditions” (whatever that is), additional licences, separate licences, etc.
Managed firewall for small business
If your business has a firewall or network security requirement, or if you need help designing, sizing and procuring the right solution – get in touch! Our team have years of experience deploying managed firewalls for small business.
We also manage hundreds of firewalls on behalf of our customers. Firewalls and network security are covered under our IT support services. In all cases, the solution can be tailored to your exact needs and budget.

